Securing Router Logins with SSH: Difference between revisions
No edit summary |
No edit summary |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
'''Securing Router Logins with SSH'''This is a walk through to help new students learn how to configure a more secure login with a router and utilize SSH. | '''Securing Router Logins with SSH''' This is a walk through to help new students learn how to configure a more secure login with a router and utilize SSH. | ||
'''ADAM NELSON''' | |||
'''DAN MARTINEAU''' | |||
'''MIKE GARIN''' | |||
==Checking Router Bin file== | ==Checking Router Bin file== | ||
| Line 9: | Line 16: | ||
[[File: | [[File:ssh.1.jpg|800px]] | ||
| Line 23: | Line 30: | ||
[[File: | [[File:ssh.ena.jpg|800px]] | ||
| Line 32: | Line 39: | ||
[[File: | [[File:ssh.config.jpg|800px]] | ||
| Line 41: | Line 48: | ||
[[File: | [[File:ssh.hostname.jpg|800px]] | ||
| Line 50: | Line 57: | ||
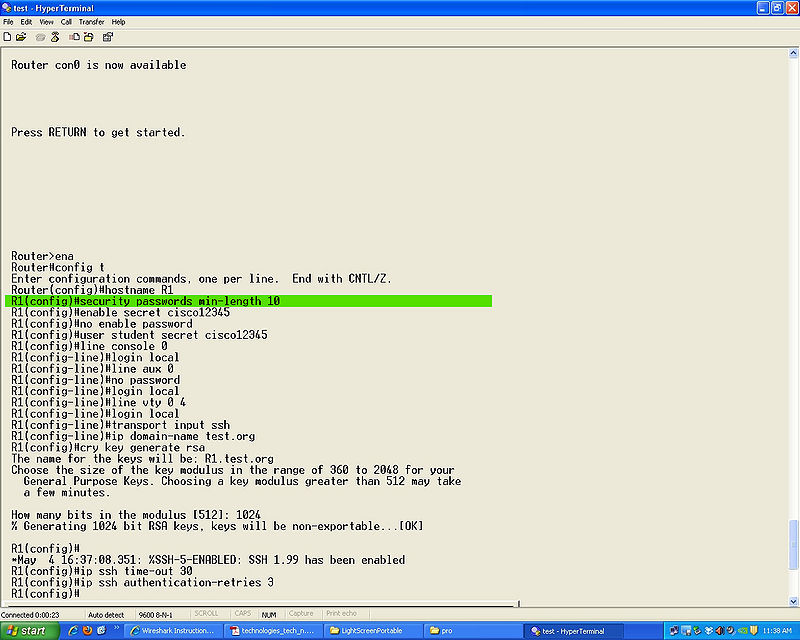
[[File: | [[File:ssh.passlength.jpg|800px]] | ||
| Line 59: | Line 66: | ||
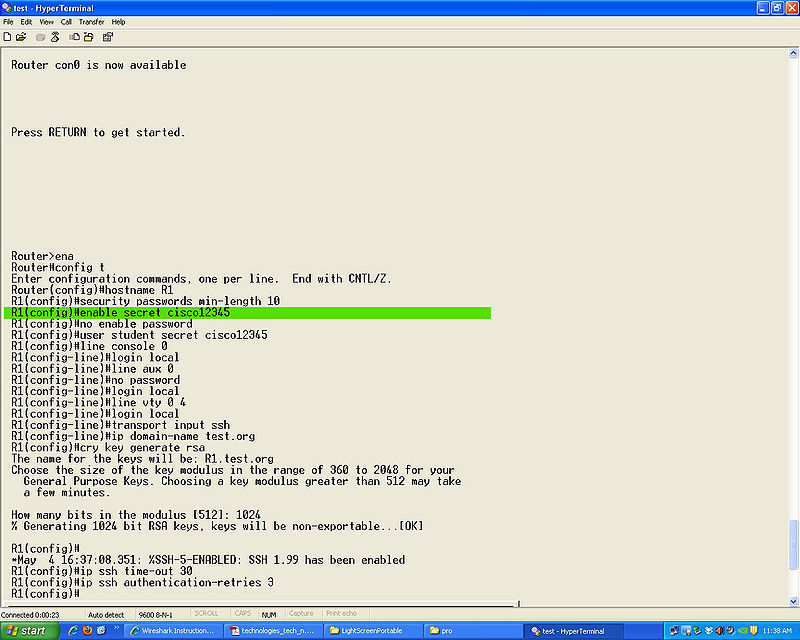
[[File: | [[File:ssh.enablesecret.jpg|800px]] | ||
| Line 68: | Line 75: | ||
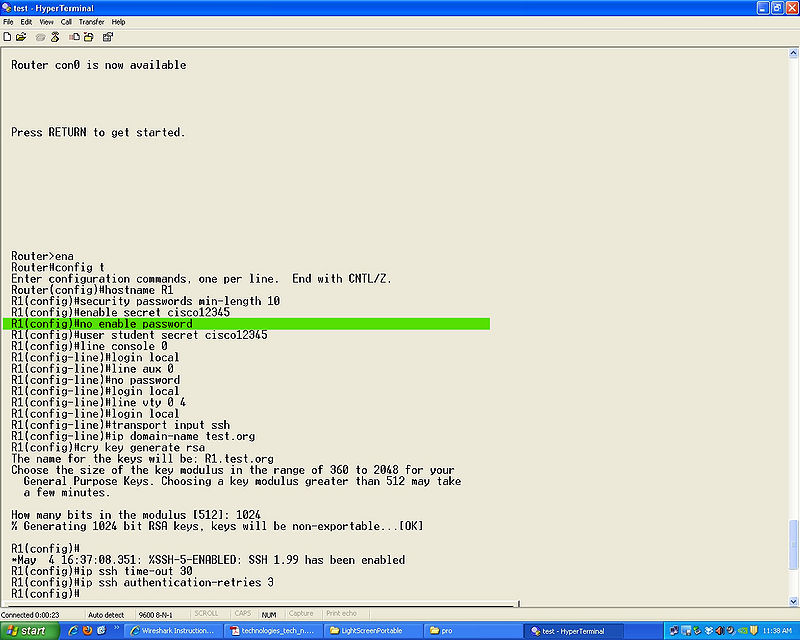
[[File: | [[File:ssh.clearpass.jpg|800px]] | ||
| Line 77: | Line 84: | ||
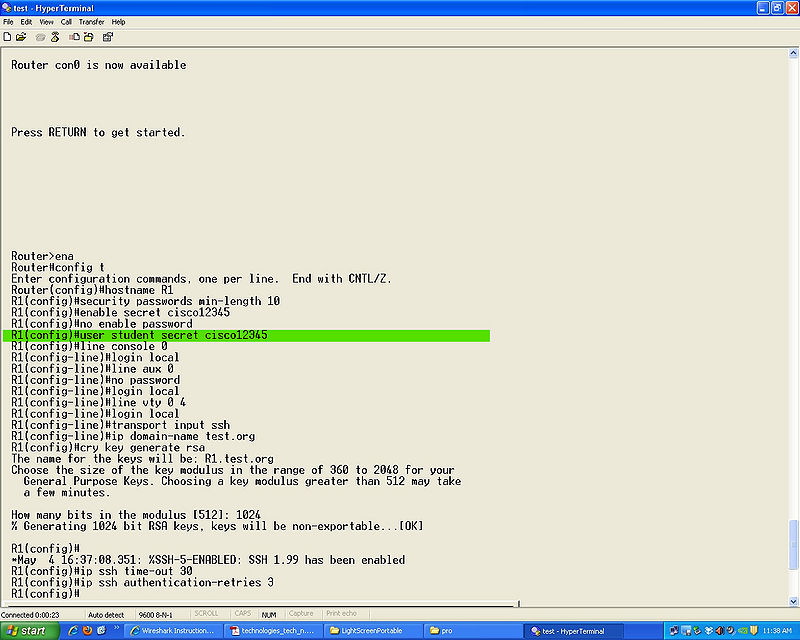
[[File: | [[File:ssh.userpass.jpg|800px]] | ||
| Line 83: | Line 90: | ||
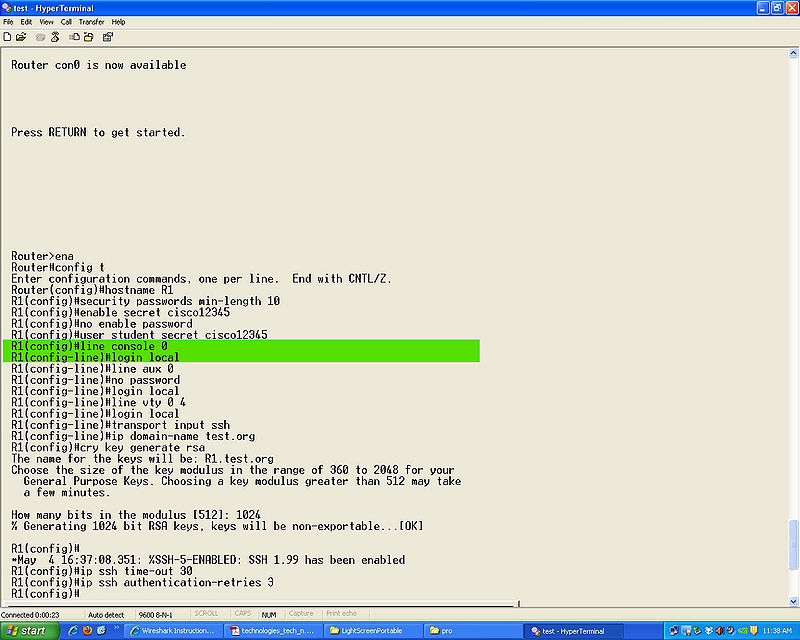
*Step 8 | *Step 8 | ||
'''line console 0''' | '''line console 0''' | ||
'''login local''' | '''login local''' | ||
[[File: | [[File:ssh.lineconsole.jpg|800px]] | ||
| Line 93: | Line 102: | ||
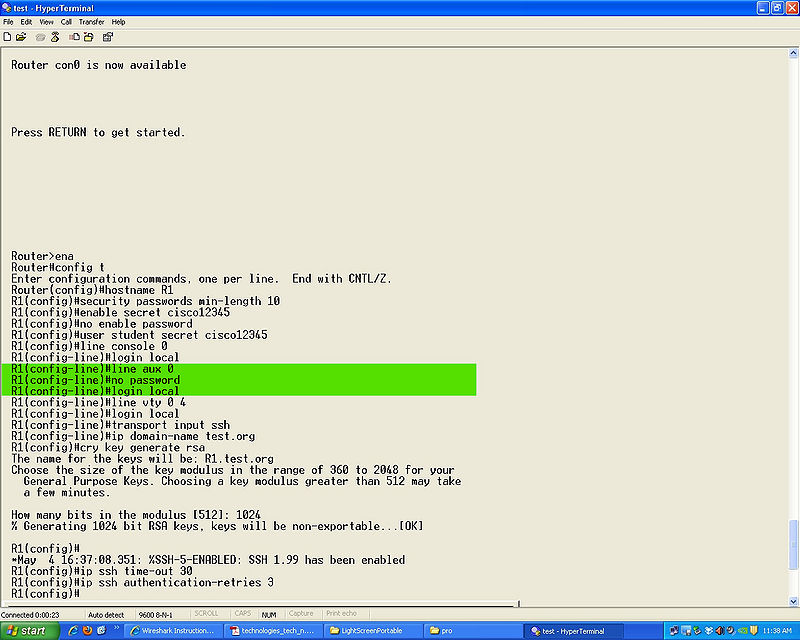
*Step 9 | *Step 9 | ||
'''line aux 0''' | '''line aux 0''' | ||
'''no password''' | '''no password''' | ||
'''login local''' | '''login local''' | ||
[[File: | [[File:ssh.lineaux.jpg|800px]] | ||
| Line 104: | Line 117: | ||
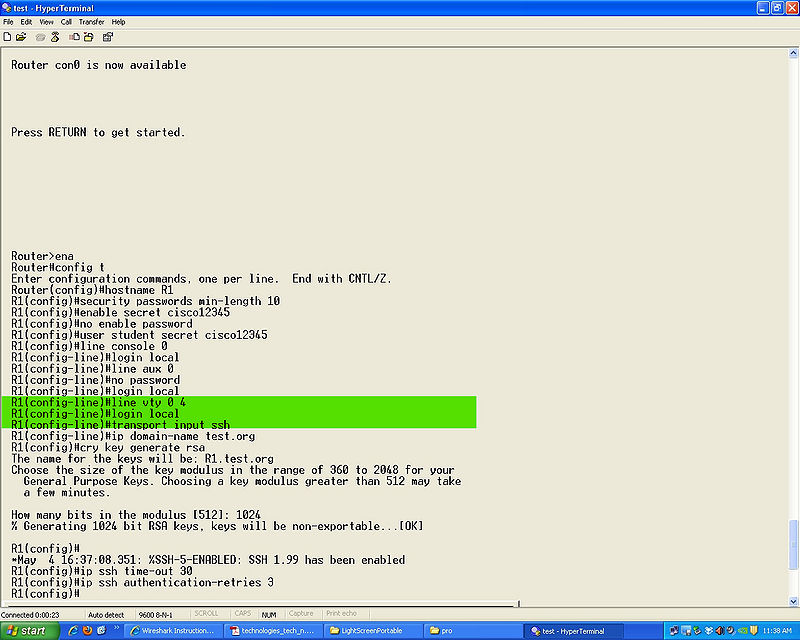
*Step 10 | *Step 10 | ||
'''line vty 0 4''' | '''line vty 0 4''' | ||
'''login local''' | '''login local''' | ||
'''transport input ssh''' this last command is to use ssh and not telnet. | '''transport input ssh''' this last command is to use ssh and not telnet. | ||
[[File: | [[File:ssh.linevty.jpg|800px]] | ||
| Line 118: | Line 135: | ||
[[File: | [[File:ssh.domainname.jpg|800px]] | ||
| Line 124: | Line 141: | ||
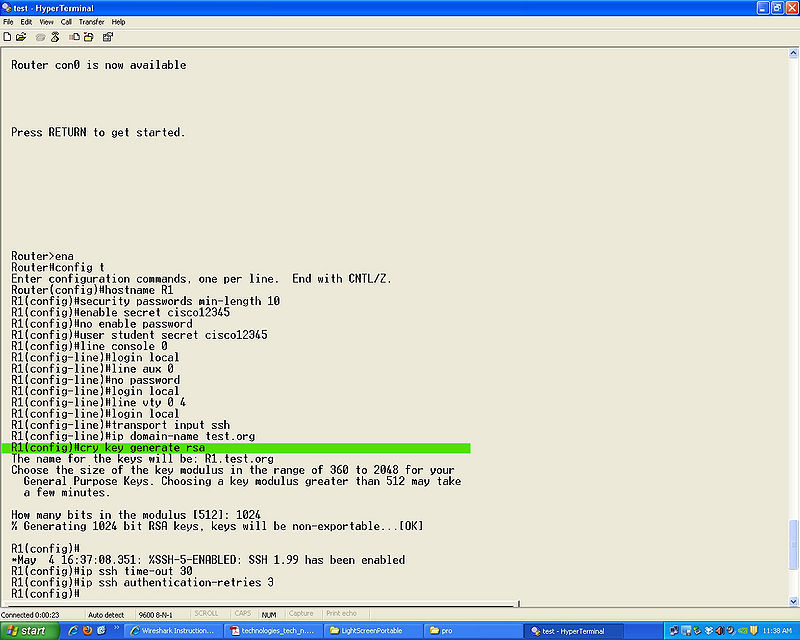
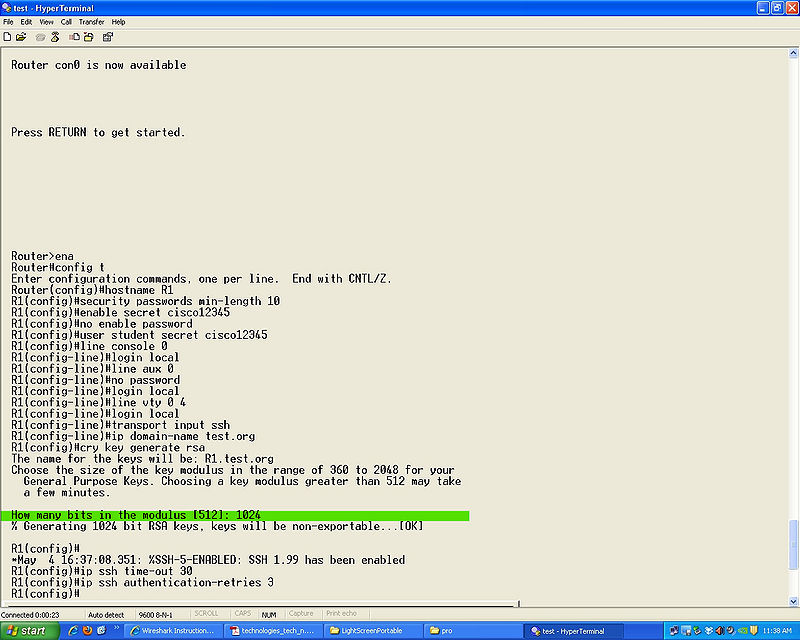
*Step 12 | *Step 12 | ||
'''cry key generate rsa''' | '''cry key generate rsa''' | ||
'''(360-2048)''' you will use this to set the size of the key the larger the more secure. | |||
[[File:ssh.keygen.jpg|800px]] | |||
[[File:ssh.bits.jpg|800px]] | |||
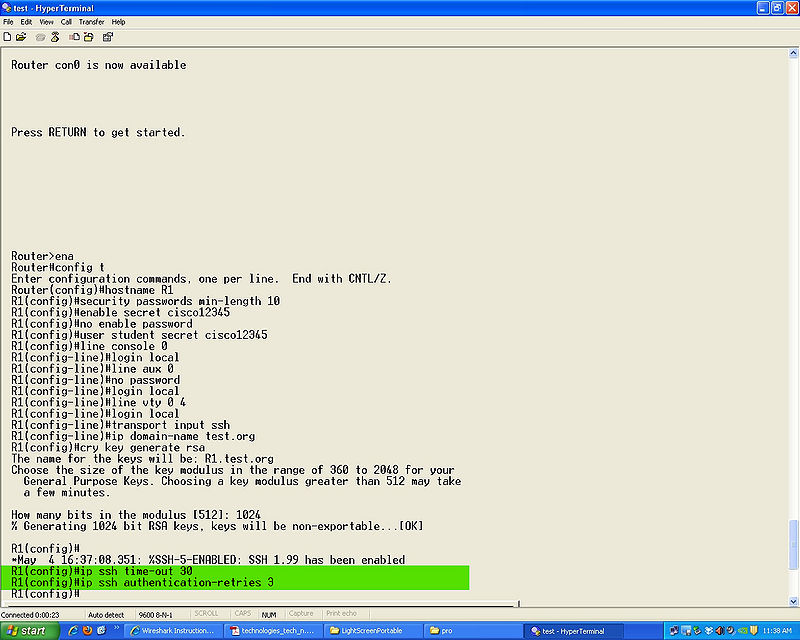
*Step 13 | |||
* | '''ip ssh time-out (number)''' | ||
'''ip ssh authentication-retries (number)''' | |||
[[File:ssh.timeoutretries.jpg|800px]] | |||
==SSH Through Putty== | |||
=== | |||
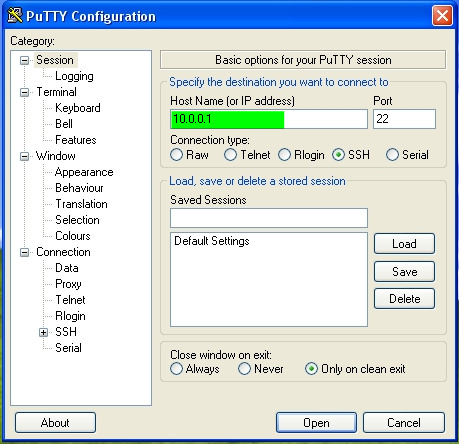
*Step 1 | *Step 1 | ||
You will login using the IP of the router you are connecting to. | |||
[[File:ssh.2.jpg|800px]] | |||
[[File: | |||
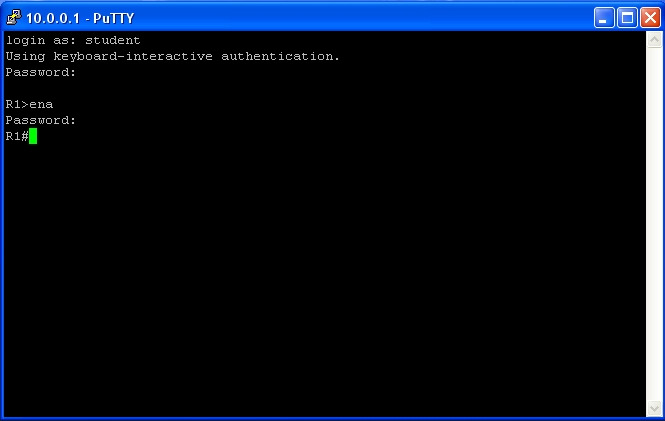
*Step 2 | *Step 2 | ||
Login using the user name and password created previously. | |||
Go to enable mode and enter your password. You are now using secure SSH. | |||
[[File:ssh.3.jpg|800px]] | |||
==External links== | ==External links== | ||
*[http://www.cisco.com/en/US/tech/tk583/tk617/technologies_tech_note09186a00800949e2.shtml Cisco Info] | |||
*[http://www. | |||
Latest revision as of 17:14, 4 May 2010
Securing Router Logins with SSH This is a walk through to help new students learn how to configure a more secure login with a router and utilize SSH.
ADAM NELSON
DAN MARTINEAU
MIKE GARIN
Checking Router Bin file
This is a check to ensure that the router you are using is going to run SSH.
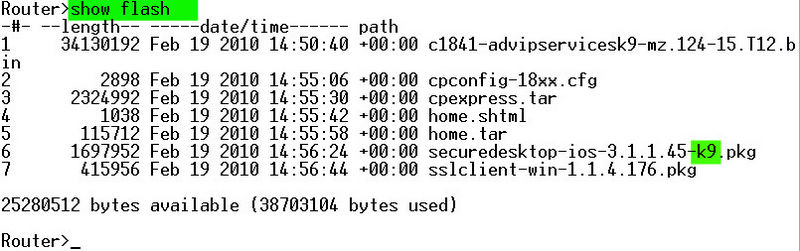
- Step 1
Issue the command show flash, to check and see if K9 is in the bin file
Router Configuration
This will cover the commands needed to setup the router logins and SSH.
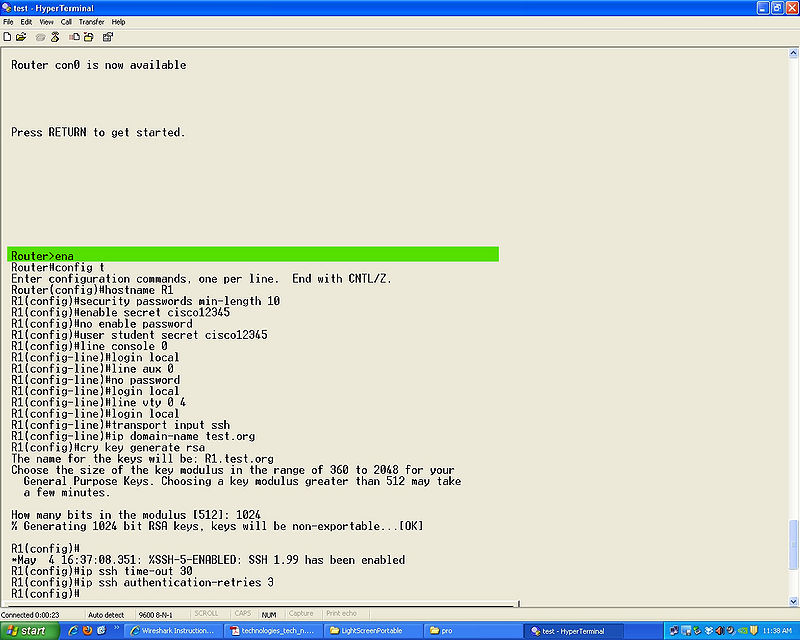
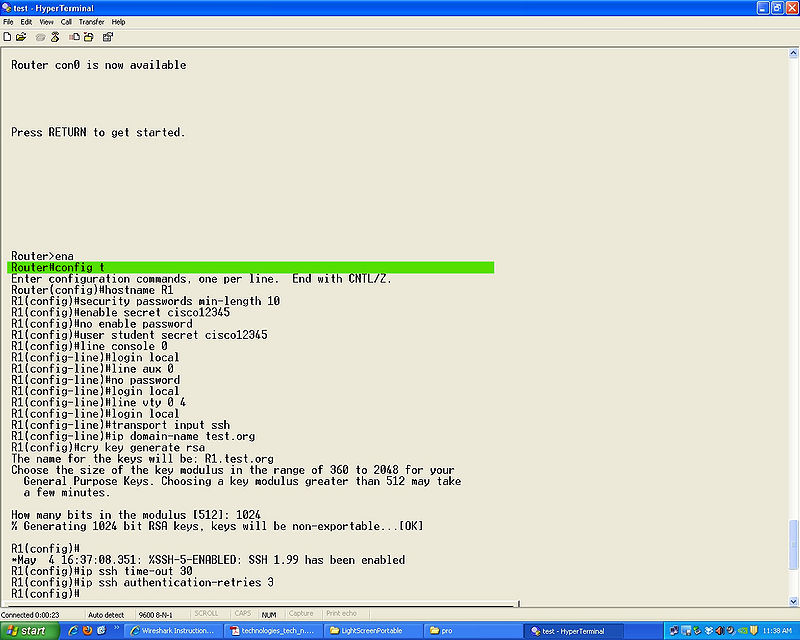
- Step 1
enaable
- Step 2
config t
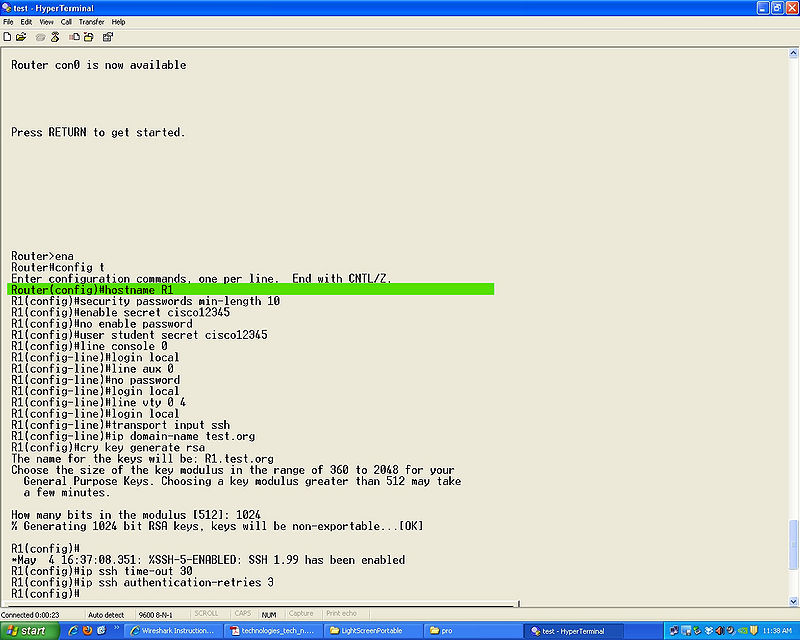
- Step 3
hostname (name)
- Step 4
security passwords min-length (number), we used 10 for a password length of 10 characters.
- Step 5
eable secret (password)
- Step 6
no enable password to clear passwords that may already be set.
- Step 7
user (name) secret (password) this will be your user name and password for loging in to the router and SSH.
- Step 8
line console 0
login local
- Step 9
line aux 0
no password
login local
- Step 10
line vty 0 4
login local
transport input ssh this last command is to use ssh and not telnet.
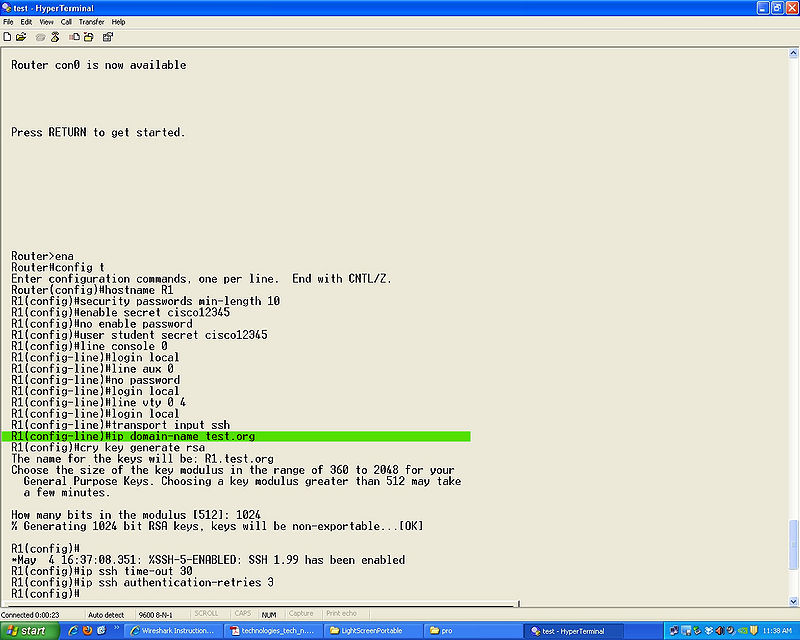
- Step 11
ip domain-name (domain name)
- Step 12
cry key generate rsa
(360-2048) you will use this to set the size of the key the larger the more secure.
- Step 13
ip ssh time-out (number)
ip ssh authentication-retries (number)
SSH Through Putty
- Step 1
You will login using the IP of the router you are connecting to.
- Step 2
Login using the user name and password created previously.
Go to enable mode and enter your password. You are now using secure SSH.