Openvpn: Difference between revisions
No edit summary |
No edit summary |
||
| Line 61: | Line 61: | ||
== Configuring the server and clients == | == Configuring the server and clients == | ||
this part can get kinda crazy on editing the text files for each system. making this easier on ourselfs we will copy the sample configuration files from the download to make life easy. take note that the server.conf file is zipped. | 1.this part can get kinda crazy on editing the text files for each system. making this easier on ourselfs we will copy the sample configuration files from the download to make life easy. take note that the server.conf file is zipped. | ||
''cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz ./ | ''cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz ./ | ||
| Line 68: | Line 68: | ||
''cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf ./'' | ''cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf ./'' | ||
*unzipping the server.conf file with | |||
''gunzip server.conf.gz'' | |||
2.since we moved all the certificates around we now need to edit the server file to point to the right location to access the certificates. | |||
''nano server.conf'' | |||
scroll down a bit untill you reach the part that looks like this: | |||
''ca ca.crt | |||
cert server.crt | |||
key server.key'' | |||
Revision as of 18:36, 12 May 2010
Steps to setting up a VPN on a Ubuntu server
1. First install the openvpn software with the command.
aptitude install openvpn
- all of the files will be located in the:
/etc/openvpn
2. to make things easier you can copy the dir "easy-rsa" from the samples dir to the current dir of "/etc/openvpn".
cp -R /usr/share/doc/openvpn/examples/easy-rsa/ ./
3. after copying the easy-rsa dir switch to easy-rsa/2.0/ where we will build the Certificates of Authority with some scripts provided.
4. edit the vars file and add in information for KEY_COUNTRY, KEY_PROVINCE, KEY_CITY, KEY_ORG, and KEY_EMAIL parameters. save and exit out back to easy-rsa/2.0/.
Nano vars
- then after you edit the file use the command source vars
5. now we are going to run some scripts starting with the clean-all
./clean-all
- followed up by the
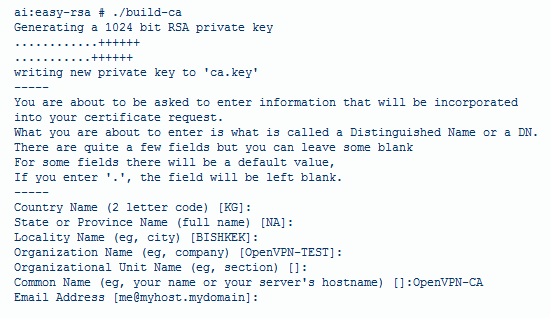
./build-ca
- the text showing up should look somewhat like this
- this picture will not look 100% like your printout based on the facts that you changed the country, city etc from the vars file, and the CA key is finished.
6. time to make the server key with the script
./build-key-server server
- you will be prompted the same message as above but you will have the added Sign the Certificate which you want to say yes.
7. the last key required is the client key and is created by doing
./build-key client1
- this will create a key for the first client and if you want more just name it "client2" for the next one. also don't forget the get the client key signed.
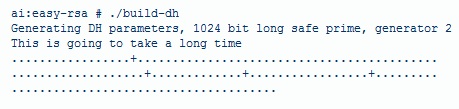
8. the DH(Diffie Hellman) parameters need to be genterated for the OpenVPN server
./build-dh
- this really does take a long time depending on the machine so take a bathroom break or something.
9. after all that you are ready to copy all those keys you have created and transfer them to a client computer. if you are having problems finding a way to copy the files think about using Filezilla and connecting to the server to the 22 port.
Configuring the server and clients
1.this part can get kinda crazy on editing the text files for each system. making this easier on ourselfs we will copy the sample configuration files from the download to make life easy. take note that the server.conf file is zipped.
cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz ./
- then for client configuration
cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf ./
- unzipping the server.conf file with
gunzip server.conf.gz
2.since we moved all the certificates around we now need to edit the server file to point to the right location to access the certificates.
nano server.conf
scroll down a bit untill you reach the part that looks like this:
ca ca.crt cert server.crt key server.key