How to Setup Security on a Home Wireless Router
- This is a "how to" article on home wireless routers. the screen shots from this article are based off of a wireless G router. This article will help in identifying the general layout of some home routers, but will also idnetify what most home routers are capable security wise.
Securing the home router
- Wireless Tab
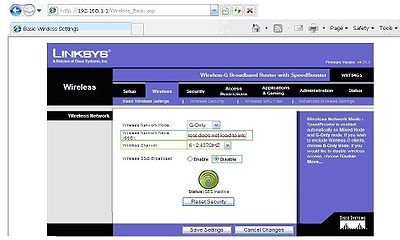
The first big step to preventing unwanted guests on to your private network is to disable wireless SSID broadcast, so it makes it harder to access by uninvited users. To disable the SSID broadcast enter into your internet browser and enter http://your.wireless.router.ipaddress. When you first start your new router this is found in the documentation of the router, as you can see in the image the router I am using has the ip address of 192.168.1.1 which is the standard for Linksys™. To find SSID broad cast click on wireless tab, there should be a basic wireless setting sub-tab. In newer models you might have to select manual setup. When disabling the SSID, you must decide on a new SSID name. Make sure it has no affiliation with your street address. After the SSID is entered select the SSID disable then save your settings and click continue on the next screen that shows. This will disable the ability to view your network name in your available wireless networks when you connect to a new network. I will address how to connect to your network later in this how to guide.
Please note: disabling SSID will make it difficult for I-phones ™ and similar wireless enabled cell phones to connect automatically.
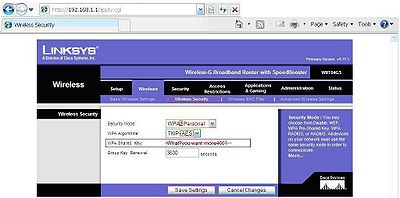
Secure your network with an access key using WPA2 personal mode, along with AES algorithm because AES is more secure than TKIP. Do not use the key I have in the following image because this document is available to others. Follow the minimum and maximum requirements the more complex the key the more secure it is, however the more complex it is, it will be harder to remember. Use capital and lowercase letters and numbers combined to make a strong password. Make sure you use a password that has a few more characters than the minimum requirements. All of this can be found in the wireless security tab.
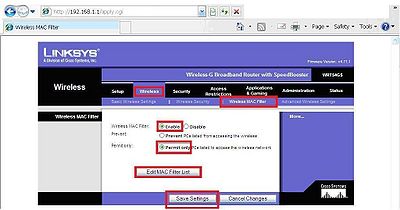
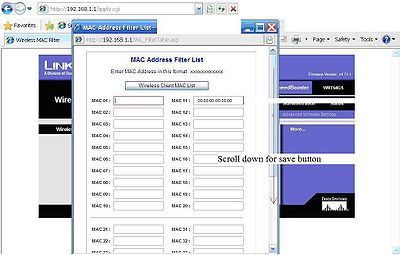
MAC address filtering was created to fill a void of lack of wireless security. I do not suggest using this due to the difficulty of manually adding MAC addresses in the router through the browser. If you decide to activate this you should know that MAC address can be forged and it is easily done on wireless networks, this is known as “spoofing”. In addition if a laptop is turned off, the computer that is using the spoofed address can easily access the network if other security is turned off. If you insist on activating this, it can be done through the wireless MAC filter sub-tab under the wireless tab. Click enable permit only and enter manually all of the MAC addresses on your wireless network by way of edit MAC filter list button. Once entered in the filter list click save before you exit the list, followed by save in the wireless MAC filter sub-tab, then continue. MAC addresses should have a format something like this 00:00:00:00:00:00 this will be an alpha numeric combination address. The next 2 screenshots show these steps.
- Security Tab
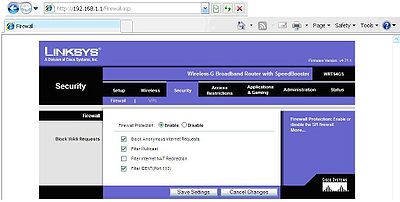
Firewall and VPN settings can be found under the security tab and will help for a first line of defense. Enabling the firewall will help in protecting your network the standard settings should automatically be enabled. Blocking anonymous requests will help make sure people are not able to find your router. Filtering multicast will disable mass requests to find multiple users on the network. In more recent routers you have the choice of blocking cookies, active x, java, and a couple of other downloading items. This consequently can disable the internet entirely if all of them are selected.
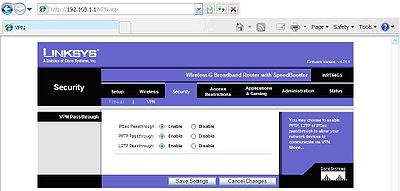
VPN settings are here to help you have a secure connection with your business for safer working at home. Check with your company to make sure that you have the right options enabled.
- Access Restrictions Tab
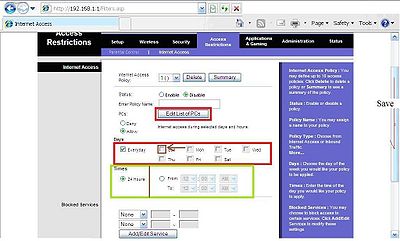
Access restrictions tab and internet access sub-tab are very useful in securing wireless information for the conscious home family. The network administrator can set access to the internet by blocking out time slots of when children are supposed to be asleep. There are many ideas to implement this section of security which the list is extensive and I will not go through. You can allow or deny access to certain pc’s that use the internet or do not use the internet. Deny internet access at night if you have certain sleep schedule. Block problem internet keywords or sites that people are using that are slowing internet access or commonly popping up. Save the list before you exit the list. Save your settings before moving to another tab.
- Applications and Gaming Tab
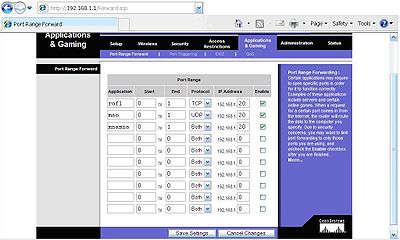
Port ranges open up security settings are too tight by opening ports that are needed to make applications run. Check with your application manufacturer for specific ports that need to be opened. Then add the ip address or address range that the computer(s) that are using that specific application. Select enable on all edited fields click save, then continue.
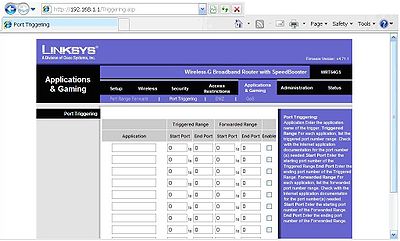
Set port triggering to prevent hackers from doing bad deeds. This will be provided by the application manufacturer. This will help prevent hacking through games and voice over internet applications. Select enable on all entered fields click save, then continue.
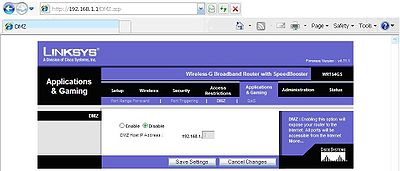
DMZ when enabled will expose the selected computer to the full unedited power of the internet. Do this with caution. This is mostly used for diagnostic purposes to prove internet access can be accessed to the selected computer when security is too tight.
- Administration Tab
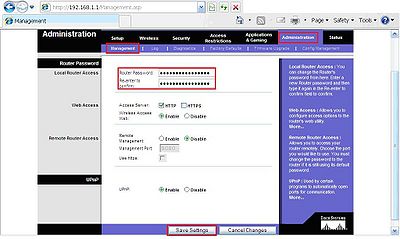
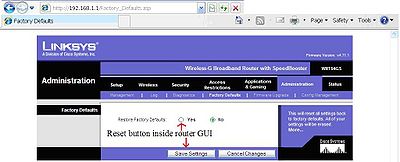
Setting a router password is critical. If your network key is weak make this one strong. If they can access the internet through your router, they can access the router. Be sure they can’t mess with the router settings or else you might have to reprogram the router entirely. The small reset button on the back will help in doing this, use the handy dandy computer repairman’s tool the paperclip if needed. Sometimes having a copy of the settings that made your network stable on a separate non pc connected to a storage drive would be a good idea. The second photo is to show how to reset your home router from inside the home router.
- Status tab
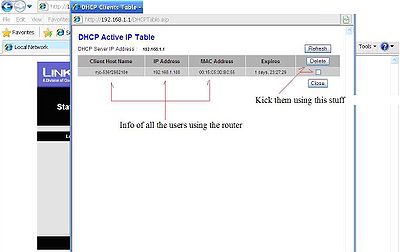
The next photo shows everyone that has access to your network. This does not show who has internet connectivity, just router connectivity. You can boot unwanted guests from your network using this table. Also, using this information will help in banning a pc, ip address, or mac addresses. Clicking the empty box will make a check mark in the box on that computer. If you click delete it will boot that person from the router temporarily. Click close or the big red x to close this window. This is under the Status tab under local network sub tab.
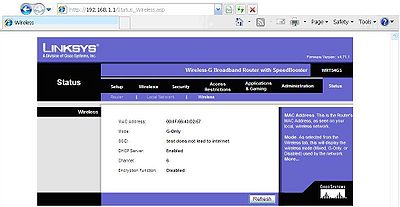
Click the status tab then click the wireless sub-tab. This will confirm that you have setup an SSID, a password to the network, and encryption for that password. This will show you the wireless channel and what wireless type the home router is transmitting: A, B, G, N, mixed mode, or single transmission type.
--Connecting a very short brief of the pc perspective--
- Setting up a wireless connection for your pc
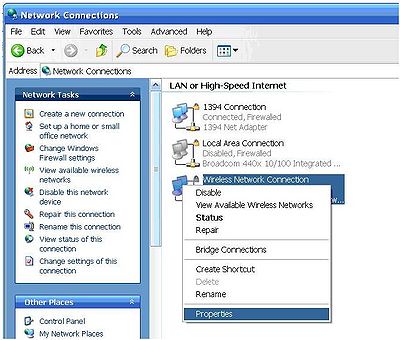
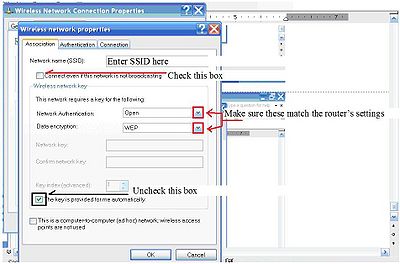
Here is how to connect to a wireless router with SSID disabled. Control panel-> network connections->wireless network connections-> right click, then left click properties.
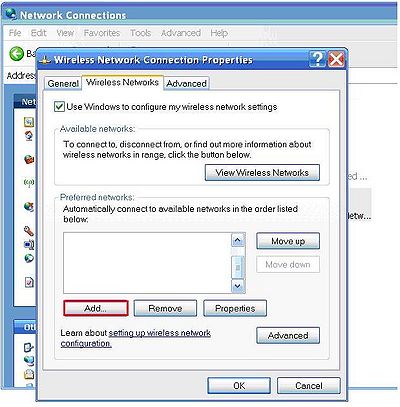
Under the wireless networks tab click add.
Enter the network SSID that was given to your network. Check the box next to the phrase “connect even if this network is not broadcasting”. Click the network authentication type and data encryption type that was designated previously. If the network key can’t be entered, check the box next to the phrase “the key is provided to me automatically”, then enter the network password and confirm the network key. You should have access to your router.