Digital Certificates in Asymmetrical Cryptography: Difference between revisions
No edit summary |
No edit summary |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
==Asymmetrical cryptography fundamentals== | ==Asymmetrical cryptography fundamentals== | ||
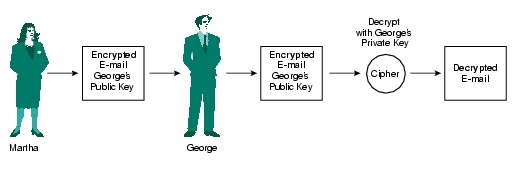
The primary feature of public-key cryptography is that it removes the need to use the same key for encryption and decryption. Whereas traditional cryptography uses one key to decode and encrypt messages, asymmetric encryption utilizes two mathematically linked key pairs; a public key and a private key which must be used together to create a connection. The public key is known to everyone and can be freely | The primary feature of public-key cryptography is that it removes the need to use the same key for encryption and decryption. Whereas traditional cryptography uses one key to decode and encrypt messages, asymmetric encryption utilizes two mathematically linked key pairs; a public key and a private key which must be used together to create a connection. The public key is known to everyone and can be freely [[Image: Wswpf_33.jpg|left]]distributed, while the private key is only known the the user who is sending the message. When someone wishes to send a message using any asymmetrical encryption standard, he must use the receiver's public key to send it, then the receiver uses his own private key to decrypt it. Additionally, the connection works both ways; as a message encrypted by a person's private key can be unencrypted by the corresponding public key. | ||
[[Image: Wswpf_33.jpg|left]] | |||
distributed, while the private key is only known the the user who is sending the message. When someone wishes to send a message using any asymmetrical encryption standard, he must use the receiver's public key to send it, then the receiver uses his own private key to decrypt it. Additionally, the connection works both ways; as a message encrypted by a person's private key can be unencrypted by the corresponding public key. | |||
A disadvantage of public-key crypography is that it is slower than symmetric encryption. It requires far more processing power to both encrypt and decrypt the contents of a message. Symmetrical algorithms are very easy to use and have the advantage of not consuming too much computing power, however there are dangers of the single secret key falling into wrong hands. Therefore, many computer companies use them in tandem. | A disadvantage of public-key crypography is that it is slower than symmetric encryption. It requires far more processing power to both encrypt and decrypt the contents of a message. Symmetrical algorithms are very easy to use and have the advantage of not consuming too much computing power, however there are dangers of the single secret key falling into wrong hands. Therefore, many computer companies use them in tandem. | ||
| Line 10: | Line 8: | ||
==Digital certificates== | ==Digital certificates== | ||
A Digital Certificate (also known as a public-key certificate)is a form of electronic credentials that associates a public key with an identity by a trusted third party. The third party verifies the owner and that the public key belongs to an owner. A digital Certificate is a pair of files on your computer. Parts of a digital certificate include: | A Digital Certificate (also known as a public-key certificate)is a form of electronic credentials that associates a public key with an identity by a trusted third party. The third party verifies the owner and that the public key belongs to an owner. A digital Certificate is a pair of files on your computer and operates under the public key infrastructure; a framework of all entities involved in digital certificate management. Parts of a standard X.509 digital certificate include: | ||
[[Image: CertificateError2.png|right]] | [[Image: CertificateError2.png|right]] | ||
| Line 23: | Line 21: | ||
Besides standard e-email transactions, Digital Certificates can be used to encrypt HTTPS communications on the internet. A web browser can obtain a certificate from a website using SSL to determine the security of a web server and whether the server has been compromised. The browser requests a certificate using a certificate signing request that has the web site name, contact email address, and company information while the site asks for information to compare it to. The owner then signs it, making the certificate a public certificate. | Besides standard e-email transactions, Digital Certificates can be used to encrypt HTTPS communications on the internet. A web browser can obtain a certificate from a website using SSL to determine the security of a web server and whether the server has been compromised. The browser requests a certificate using a certificate signing request that has the web site name, contact email address, and company information while the site asks for information to compare it to. The owner then signs it, making the certificate a public certificate. | ||
===Digital Signatures=== | ===Digital Signatures=== | ||
Asymmetric cryptography cannot naturally provide authentication: as although a message that is sent with an asymmetric protocol can ensure the message has not been tampered with, it cannot verify whether the sender is who they say they are due to a public key's nature. To provide proof, a digital signature must be created (not to be confused with a digital certificate), which acts as a handwritten signature verifying the sender. It can also confirm that the message had not been altered since it was signed, or prevent the sender from disputing the origin of the message. Hashing, in its | Asymmetric cryptography cannot naturally provide authentication: as although a message that is sent with an asymmetric protocol can ensure the message has not been tampered with, it cannot verify whether the sender is who they say they are due to a public key's nature. To provide proof, a digital signature must be created (not to be confused with a digital certificate), which acts as a handwritten signature verifying the sender. It can also confirm that the message had not been altered since it was signed, or prevent the sender from disputing the origin of the message. The purpose of a digital signature is to only show the that the public key labeled as belonging to a person was used to encrypt the message, nothing more. Hashing, in its simplest form is an algorithm that you can run a piece of data through and get out a number that represents the original. | ||
A digital signature consists of three algorithms: A key generation algorithm that selects a private key at random from a set of possible private keys, then uses it to create the private key and public key that corresponds to it; a signing algorithm that produces the signature when given a message and a private key, and a signature verifying algorithm that takes the message, public key and signature either accepts or rejects the message's claim of authenticity. | A digital signature consists of three algorithms: A key generation algorithm that selects a private key at random from a set of possible private keys, then uses it to create the private key and public key that corresponds to it; a signing algorithm that produces the signature when given a message and a private key, and a signature verifying algorithm that takes the message, public key and signature either accepts or rejects the message's claim of authenticity. | ||
===Hashing=== | ===Hashing=== | ||
Hashing is a form of cryptographic security which | Hashing is a form of cryptographic security which can be used to ensure the integrity of a file by guaranteeing no one has tampered with it. Where as encryption has a two step process used to first encrypt and then decrypt a message, hashing condenses a message into a irreversible fixed-length value, or hash. Two of the most common hashing algorithms seen in networking are MD5 and SHA-1; however, they are both found to have vulnerabilities and should be discouraged. | ||
==Certificate Life Cycle== | |||
Digital certificates are removed and added with changes in a companies's network, adding or subtracting users, or privilege changes. As such, certificates are given a lifetime consisting of four stages: Creation, Suspension, Revocation, and Expiration. | |||
**Creation: A user is positively verified and a certificate is created and issued to the user by the Certificate Authority. The CA applies a signature to the certificate and can continually update the certificate. | |||
**Suspension: In the case of a user's absence or vulnerability of the server connected to the certificate, a certificate can be suspended until a later date. On the user's return, the certificate can be reinstated or revoked. | |||
**Revocation: This state may be brought on a vulnerability or a situation where the user's private key may be compromised. The certificate is no longer valid and it is placed into a public repository by either the CA or a user and forgoes expiration. | |||
**Expiration: At this stage, a certificate can no longer be used. Every certificate issued by the CA must have an expiration date. An expired certificate cannot be renewed and a user must follow a process to be granted a new certificate. | |||
==Certificate Authority== | |||
The CA or Certificate authority is a third party agency which manages the distribution of Digital Certificates and is trusted by both the owner and receiver of a certificate. A certificate authority has the responsibilities of: | |||
*Publishing the criteria for granting, revoking, and managing certificates. | |||
*Distributing CA certificates | |||
*Generating, issuing, and distributing public key certificates to applicants. | |||
*Managing certificates (for example, enrolling, renewing, and revoking them). | |||
*Verifying evidence submitted by applicants. | |||
*Providing a means for applicants to request revocation | |||
*Maintaining the security, availability, and continuity of the certificate issuance signing functions. | |||
*Time stamping a digital signature. | |||
==Types of Digital Certificates== | |||
There are five categories of digital certificate. The common categories are personal digital certificates, server digital certificates, adn software publisher digital certificates. | |||
===Class 1: Personal Digital Certificates=== | |||
Personal Digital Certificates are used by individuals when they exchange messages with other users or online services, such as Web Browsers and S/MIME applications. | |||
===Class 2: Serer Digital certificates=== | |||
Server Certificates enable Web servers to operate in a secure mode. A Server Certificate unambiguously identifies and authenticates your server and encrypts any information passed between the server and a Web browser. A server digital certificate can perform two functions: ensure authenticity of a web server and enable clients connecting to a web server to examine the identity of a server's owner. | |||
===Class 3: Software Publisher Digital Certificates=== | |||
Publisher Digital Certificates use validation to provide customers with the information and assurance they need when downloading software from the Internet. They are used by software publishers to ensure their software has not been tampered with | |||
===Dual-Key and Dual-Sided Digital Certificates=== | |||
Dual-key certificates are intrinsically linked certificates that split the functionality of a single certificate between two. The signing certificate is used to sign a message and prove its identity is authentic, while the encryption certificate is used to encrypt the message. A copy of an encryption certificate should always be kep to enable email decryption, but a copy of the signign certificate is not required, although at the cost of reduced security.Dual keys enable a more secure system for backing up certificates. | |||
Dual-Sided certificates allow a client to authenticate a verifiable certificate back to a server. Certain situations, such as in a corporate military/financial setting where in addition to a username and password a user must first authenticate a computer in the same way a website authenticates itself to you. | |||
===X.509 Digital Certificates=== | |||
X.509 is the most widely used standard for digital certificates. The X.509 standard specifies formats for Public Key certificates. Layout of this digital certificate can be found above. | |||
===Wildcard Certificates=== | |||
Wildcard certificates are a sub-type of digital certificates that encompass an entire domain of website addresses. This is useful in situations where a client cannot differentiate between two different hosts it has to query at the same time. | |||
Latest revision as of 21:43, 8 December 2011
As part of protection and encryption of ever increasing network vulnerabilities and security needs, traditional symmetrical algorithms that encrypt information using private keys are not always sufficient. Asymmetric Cryptography, also known as Public Key Cryptography uses two keys instead of one, and contains many more permutations and defenses than an ordinary symmetrical algorithm. The use of these algorithms also allows checks of authenticity with digital signatures.
Asymmetrical cryptography fundamentals
The primary feature of public-key cryptography is that it removes the need to use the same key for encryption and decryption. Whereas traditional cryptography uses one key to decode and encrypt messages, asymmetric encryption utilizes two mathematically linked key pairs; a public key and a private key which must be used together to create a connection. The public key is known to everyone and can be freely
distributed, while the private key is only known the the user who is sending the message. When someone wishes to send a message using any asymmetrical encryption standard, he must use the receiver's public key to send it, then the receiver uses his own private key to decrypt it. Additionally, the connection works both ways; as a message encrypted by a person's private key can be unencrypted by the corresponding public key.
A disadvantage of public-key crypography is that it is slower than symmetric encryption. It requires far more processing power to both encrypt and decrypt the contents of a message. Symmetrical algorithms are very easy to use and have the advantage of not consuming too much computing power, however there are dangers of the single secret key falling into wrong hands. Therefore, many computer companies use them in tandem.
Digital certificates
A Digital Certificate (also known as a public-key certificate)is a form of electronic credentials that associates a public key with an identity by a trusted third party. The third party verifies the owner and that the public key belongs to an owner. A digital Certificate is a pair of files on your computer and operates under the public key infrastructure; a framework of all entities involved in digital certificate management. Parts of a standard X.509 digital certificate include:
- The person's name
- An e-mail address
- A serial number
- A public key
- The hash used to encrypt the digital certificate
- An expiration date (certificates are valid for five years)
- The signature and has algorithms
- A digital signature
Besides standard e-email transactions, Digital Certificates can be used to encrypt HTTPS communications on the internet. A web browser can obtain a certificate from a website using SSL to determine the security of a web server and whether the server has been compromised. The browser requests a certificate using a certificate signing request that has the web site name, contact email address, and company information while the site asks for information to compare it to. The owner then signs it, making the certificate a public certificate.
Digital Signatures
Asymmetric cryptography cannot naturally provide authentication: as although a message that is sent with an asymmetric protocol can ensure the message has not been tampered with, it cannot verify whether the sender is who they say they are due to a public key's nature. To provide proof, a digital signature must be created (not to be confused with a digital certificate), which acts as a handwritten signature verifying the sender. It can also confirm that the message had not been altered since it was signed, or prevent the sender from disputing the origin of the message. The purpose of a digital signature is to only show the that the public key labeled as belonging to a person was used to encrypt the message, nothing more. Hashing, in its simplest form is an algorithm that you can run a piece of data through and get out a number that represents the original.
A digital signature consists of three algorithms: A key generation algorithm that selects a private key at random from a set of possible private keys, then uses it to create the private key and public key that corresponds to it; a signing algorithm that produces the signature when given a message and a private key, and a signature verifying algorithm that takes the message, public key and signature either accepts or rejects the message's claim of authenticity.
Hashing
Hashing is a form of cryptographic security which can be used to ensure the integrity of a file by guaranteeing no one has tampered with it. Where as encryption has a two step process used to first encrypt and then decrypt a message, hashing condenses a message into a irreversible fixed-length value, or hash. Two of the most common hashing algorithms seen in networking are MD5 and SHA-1; however, they are both found to have vulnerabilities and should be discouraged.
Certificate Life Cycle
Digital certificates are removed and added with changes in a companies's network, adding or subtracting users, or privilege changes. As such, certificates are given a lifetime consisting of four stages: Creation, Suspension, Revocation, and Expiration.
- Creation: A user is positively verified and a certificate is created and issued to the user by the Certificate Authority. The CA applies a signature to the certificate and can continually update the certificate.
- Suspension: In the case of a user's absence or vulnerability of the server connected to the certificate, a certificate can be suspended until a later date. On the user's return, the certificate can be reinstated or revoked.
- Revocation: This state may be brought on a vulnerability or a situation where the user's private key may be compromised. The certificate is no longer valid and it is placed into a public repository by either the CA or a user and forgoes expiration.
- Expiration: At this stage, a certificate can no longer be used. Every certificate issued by the CA must have an expiration date. An expired certificate cannot be renewed and a user must follow a process to be granted a new certificate.
Certificate Authority
The CA or Certificate authority is a third party agency which manages the distribution of Digital Certificates and is trusted by both the owner and receiver of a certificate. A certificate authority has the responsibilities of:
- Publishing the criteria for granting, revoking, and managing certificates.
- Distributing CA certificates
- Generating, issuing, and distributing public key certificates to applicants.
- Managing certificates (for example, enrolling, renewing, and revoking them).
- Verifying evidence submitted by applicants.
- Providing a means for applicants to request revocation
- Maintaining the security, availability, and continuity of the certificate issuance signing functions.
- Time stamping a digital signature.
Types of Digital Certificates
There are five categories of digital certificate. The common categories are personal digital certificates, server digital certificates, adn software publisher digital certificates.
Class 1: Personal Digital Certificates
Personal Digital Certificates are used by individuals when they exchange messages with other users or online services, such as Web Browsers and S/MIME applications.
Class 2: Serer Digital certificates
Server Certificates enable Web servers to operate in a secure mode. A Server Certificate unambiguously identifies and authenticates your server and encrypts any information passed between the server and a Web browser. A server digital certificate can perform two functions: ensure authenticity of a web server and enable clients connecting to a web server to examine the identity of a server's owner.
Class 3: Software Publisher Digital Certificates
Publisher Digital Certificates use validation to provide customers with the information and assurance they need when downloading software from the Internet. They are used by software publishers to ensure their software has not been tampered with
Dual-Key and Dual-Sided Digital Certificates
Dual-key certificates are intrinsically linked certificates that split the functionality of a single certificate between two. The signing certificate is used to sign a message and prove its identity is authentic, while the encryption certificate is used to encrypt the message. A copy of an encryption certificate should always be kep to enable email decryption, but a copy of the signign certificate is not required, although at the cost of reduced security.Dual keys enable a more secure system for backing up certificates. Dual-Sided certificates allow a client to authenticate a verifiable certificate back to a server. Certain situations, such as in a corporate military/financial setting where in addition to a username and password a user must first authenticate a computer in the same way a website authenticates itself to you.
X.509 Digital Certificates
X.509 is the most widely used standard for digital certificates. The X.509 standard specifies formats for Public Key certificates. Layout of this digital certificate can be found above.
Wildcard Certificates
Wildcard certificates are a sub-type of digital certificates that encompass an entire domain of website addresses. This is useful in situations where a client cannot differentiate between two different hosts it has to query at the same time.