Chapter 4 Study Guide
Filesystem Hierarchy Standard
- Defines a standard set of directories, their subdirectories and file content used by Linux and UNIX
- Allows a user proficient with Linux t navigate UNIX easier.
- Gives software developers to locate files on different distributions of Linux
- Allows creation of software that is not distribution specific
Finding Files
locate command
The fasted method for finding files
The locate command searches a premade database that contains a list of all the files on the system. The database is indexed much like a text book. The database used is updated each day automatically or can be updated manually by running the updatedb command.
ex. [root@server1 ~]# locate inittab /etc/inittab /usr/share/man/man5/inittab.5.gz /user/share/vim/vim72/syntax/inittab.vim
find command
Slower but more versatile method for locating files
Does not use a premade index, but searches the directory tree recursively, starting from a certain directory, for files that meet a certain criteria.
The format of the find command is as follows:
find <start directory> -criteria <what to find>
can use many different criteria to search for files
-amin - x - searches for files that were accessed less than x minutes ago
-amin + x - searches for files that were accessed more than x minutes ago
-atime - x - searches for files that were accessed less than x days ago
-atime + x - searches for files that were accessed more than x days ago
-empty - searches for empty files or directories
-fstype x - searches for files if they are on a certain filesystem
-group x - searches for files that are owned by a certain group or GID
-inum x - searches for files that have an inode number of x
-mmin - x - searches for files that were modified less than x minutes ago
-mmin + x - searches for files that were modified more than x minutes ago
-mtime - x - searches for files that were modified less than x days ago
-mtime + x - searches for files that were modified more than x days ago
-name x - searches for a certain filename
-regexp x - searches for certain filenames using regular expressions instead of wildcards
-size - x - searches for files with a size less than x
-size + x - searches for files with a size larger than x
-size x - searches for files with a size of x
-type x - searches for files of type x where x is:
b for block files
c for character files
d for directory files
p for named pipes
f for regular files
l for symbolic links
s for sockets
-user x - searches for files owned by a certain user or GID
Modify file and directory ownership
When a user create a file or directory, that users name and primary group becomes the owner and group owner of the file.
The permission structure is affected.
It also determines the ability to modify file and directory permissions and ownership.
Only two users on a Linux system can modify permissions on a file or directory or change its ownership:
The owner of the file or directory and the root user.
Example: to view your current user name, you can type the whoami command.To view your group name you can type the groups command.
[roots@server1 -] # whoami
Root
[root@server1 -] # groups
Root bin daemon sys adm disk wheel
[root@server1 -] #_
To quickly create an empty file, you can use the touch command.
[root@server1 -] # touch file1
[root@server1 -] # ls –l
Total 4 drwx- - - - 3 root root 4096 Apr 8 07:12 Desktop
-rx-r- -r-- 1 root root 0 Apr 29 15:40 file1
[root@server1 -] #
To change the ownership of a file or directory, you can use the chown (change ownership) command. Which takes two arguments at minimum. The new owner and the files directories to change.
Both arguments can be absolute or relative pathnames, and you can change permissions recursively, throughout the directory tree using the –R option to the chown command.
To change the ownership of file1 to the user “user1” and the ownership of the directory Desktop and all its contents to “user1” as well, you can use these commands.
[root@server1 -] # chown user1 file1
[root@server1 -] # chown –R user1 Desktop
[root@server1 -] # ls –l
total 4
drwx 3 user1 root 4096 Apr 8 07:12 Desktop
-rw-r- -r- - 1 user1 root 0 Apr 29 15:40 file1
[root@server1 -] # ls -1 Desktop
Total 16
-rw- - - - - 1 user1 root 163 Mar 29 09:58 Floppy
-rw-r- -r-- 1 user1 root 163 Mar 29 09:58 Home
-rw-r- -r-- 1 user1 root 163 Mar 29 09:58 Start Here
-rw-r- -r-- 1 user1 root 163 Mar 29 09:58 Trash
[root@server1 -] #
If a regular user changes ownership of a file or directory that he owns, that user cannot gain back ownership. Instead the new owner of that fle or directory must change it to the original user. However, the previous examples involve the root user, who always has the ability to regain ownership.
[root@server1 -] # chown root file1
[root@server1 -] # chown –R root Desktop
[root@server1 -] # ls –l
total 4
drwx 3 root root 4096 Apr 8 07:12 Desktop
-rw-r- -r- - 1 root root 0 Apr 29 15:40 file1
[root@server1 -] # ls -1 Desktop
Total 16
-rw- - - - - 1 root root 163 Mar 29 09:58 Floppy
-rw-r- -r-- 1 root root 163 Mar 29 09:58 Home
-rw-r- -r-- 1 root root 163 Mar 29 09:58 Start Here
-rw-r- -r-- 1 root root 163 Mar 29 09:58 Trash
Just like the chown command. You can use the chgrp (change group) command to change group owner of a file and directory. The same rules apply.
Example:
[root@server1 -] # chgrp sys file1
[root@server1 -] # chgrp –R sys Desktop
[root@server1 -] # ls –l
total 4
drwx 3 root sys 4096 Apr 8 07:12 Desktop
-rw-r- -r- - 1 root sys 0 Apr 29 15:40 file1
[root@server1 -] # ls -1 Desktop
Total 16
-rw- - - - - 1 root sys 163 Mar 29 09:58 Floppy
-rw-r- -r-- 1 root sys 163 Mar 29 09:58 Home
-rw-r- -r-- 1 root sys 163 Mar 29 09:58 Start Here
-rw-r- -r-- 1 root sys 163 Mar 29 09:58 Trash
Note: Regular users can change the group of a file or directory only to a group they belong.
Normally, you change both the ownership and group ownership on a file that needs to be maintained by someone else. You can change both at the same time using the chown command.
To change the owner to user1 and the group owner to root for file 1 you will use these commands.
[root@server1 -] # chown user1.root file1
[root@server1 -] # chown –R user1.root Desktop
[root@server1 -] # ls –l
total 4
drwx 3 user1 root 4096 Apr 8 07:12 Desktop
-rw-r- -r- - 1 user1 root 0 Apr 29 15:40 file1
[root@server1 -] # ls -1 Desktop
Total 16
-rw- - - - - 1 user1 root 163 Mar 29 09:58 Floppy
-rw-r- -r-- 1 user1 root 3578 Mar 29 09:58 Home
-rw-r- -r-- 1 user1 root 1791 Mar 29 09:58 Start Here
-rw-r- -r-- 1 user1 root 4096 Mar 29 09:58 Trash
To protect your systems security, you should ensure that most files residing in a users home directory are owned by that user. To change the ownership back to the root user for file1 and the Desktop directory to avoid future problems. You can type the following.
[root@server1 -] # chown root.root file1
[root@server1 -] # chown –R root.root Desktop
[root@server1 -] # ls –l
total 4
drwx 3 user1 root 4096 Apr 8 07:12 Desktop
-rw-r- -r- - 1 user1 root 0 Apr 29 15:40 file1
[root@server1 -] # ls -1 Desktop
Total 16 -rw- - - - - 1 root root 163 Mar 29 09:58 Floppy
-rw-r- -r-- 1 root root 3578 Mar 29 09:58 Home
-rw-r- -r-- 1 root root 1791 Mar 29 09:58 Start Here
drwx- - - - - 2 root root 4096 Mar 29 09:58 Trash
[root@server1 -] #
Interpreting File Permissions
All files contain information regarding permissions in the “mode” Mode is broken into three sections based on the users who receive the permissions
User (owner) permissions
Group (group owner) permissions
Other (everyone else) permissions
Each of the users can be assigned different permissions
Read – allows user to open and read file
- allows user to list contents of directory (if given execute permission)
Write – allows user to open, read, and edit file
- allows user to add or remove files to and from directory (if given execute)
Execute – allows user to execute the file in memory
- allows user to enter directory and work with contents
Changing File Permissions
There are two different methods for changing file permissions
Symbolic
Numeric
Uses the “chmod” command to change permissions
The chmod command takes two arguments at minimum
The first argument specifies the criteria to change permissions The remaining arguments indicate the filename to change
Symbolic Method
You must first determine user to apply permissions to
U (user)
G (group)
O (other)
A (all categories)
Permissions can be added, subtracted, or specify exact permissions
+ adds permissions
- subtracts permissions
= defines exact permissions
Uses three permission levels
R (read)
W (write)
X (execute)
When typing the users, they are separated by commas. Also ensure that there are no spaces between any criteria.
ex
- chmod u+r,g+r,o+r file1
- chmod u-wr file1
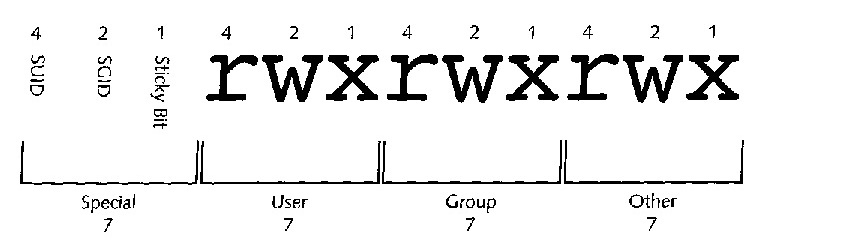
Numeric Method
Uses binary powers of two to determine permissions
Each user category assigned permissions of 0-7
R(read) = 4
W(write)=2
X(execute=1
None = 0
Add the values of desired permissions to determine the number to input
ex.
- chmod 540 file1
User has read and execute, group has read, other has none
Understand and Create linked files
What is a linked file? A link is a way of matching two or more file names to the same set of file data.
How many ways can a file be linked? 2 ways
What are they? A symbolic link, or symlic and A hard link.
How are files stored on a file system?
The structural level of a filesystem has three main sections: The superblock, The inode table and data blocks
Superblock : Is the section that contains information about the filesystem. Filesystem Type, Size, status, number of inodes.
Inodes Table: The collection of inodes for all files and directories on a filesystem. Each file in the Linux system gets its own inode. Inode(The portion of a file that holds information on the file’s attributes, access permissions, where it is located, who owns it, and file type. Each inode contains a unique inode number for identificattion purposes)
How do you view the inode number? ls -li
Data Blocks: The data that makes up the content of the file as well as the filename. Blocks are also know as allocation units.
Hard Link Characteristics
- In a hard link, two files share the same data
- Hard Link files are direct copies of one another
- Same Size
- They share the same inode and inode number
- The hard link will look and behave the same as the original.
- A file can be hard linked an unlimited number of times if the files reside on the same filesystem.
- Hardlinks can not span across partitions
- Points to a file by its inode
How do you create a Hard Link? To create a hard link you would use the ln (Link) command and specify the existing file to hard link and the target file that will be created.
Symbolic Link or symlic Charateristics
- One file is a pointer or shortcut to another file. The files may point to files located on other partitions or other network drives
- Symbolic links do not share the same inode and inode number with their target file
- Different size
- Symbolic links point to another file by its name
- Soft links do not need to reside on the same filesystem
- removing the target file for a symbolic link breaks the link and it will no longer work.
How do you create a symbolic link? To create a symbolic link you would use the ln (Link) command and use –s followed by the target file and the file you want to link.
Identify the default permissions created on files and directories
New files are given rw-rw-rw- by the system when they are created.
New directories are given rwxrwxrwx by the system when they are created.
Special Permissions
SUID Gives user who executes file temporarily ownership of a file while executing.
SGID Gives regular user who executes the file or binary compiled program temporary membership of the group that is attached to it.
Sticky Bit Prevents users who have permission to write to a directory from deleting files they did not create.
Example of setting Sticky Bit in special permissions
{root@server1 ~} # ls -l
total 12
drwx------ 2 root root 4096 May 2 21:41 dir2
{root@server1 ~} # chmod 1770 dir2
{root@server1 ~} ls –l
total 12
drwxrwx--T 2 root root 4096 May 2 21:41 dir2