Control Web Access With Squid
HOW TO CONTROL WEB ACCESS WITH SQUID
We are going to learn how to install and configure Squid on Ubuntu to restrict or allow web access on a network.
What is Squid?
Squid is a software that was developed by Duane Wessels as the Harvest object cache, part of the Harvest project at the University of Colorado at Boulder. The software was designed to run on Unix-like system, but it can also run on Windows-based system. Squid is a proxy server and web cache daemon. It can be used to speed up a web server by caching repeated requests and aiding security by filtering traffic (Control when and which IP adresses can access the web). It is primarily used for HTTP and FTP but has limited support for TLS, SSL, Internet Gopher and HTTPS.
Install Squid on Ubuntu.
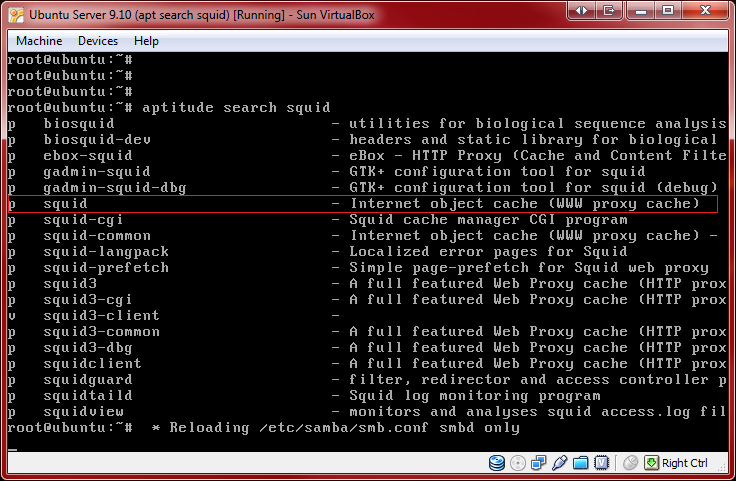
What can be done before installing Squid is to search for the software on your machine. To do so, log in as root, and enter the following commands:
root@ubuntu:~# aptitude search squid
If the command was successful, you should have a similar screen shot.
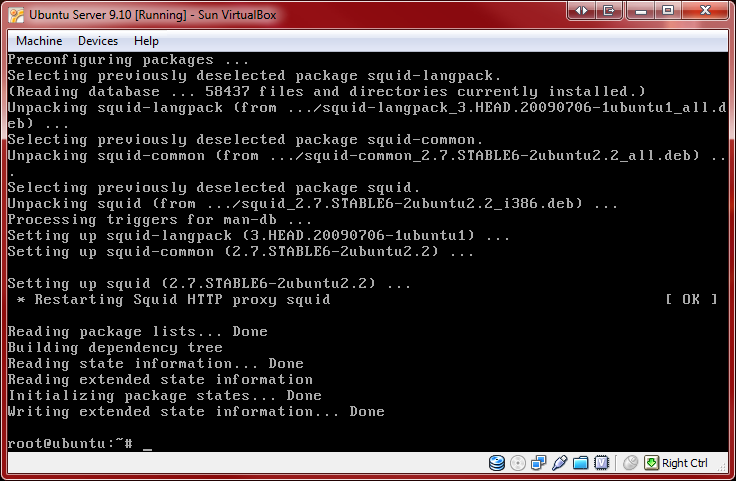
If not already installed, we can being installation by entering the following commands:
root@ubuntu:~# aptitude install squid
The next screen shot assures us that Squid was installed successfully
Starting Squid
The chkconfig squid on command can be used to configure squid to start at boot.
root@ubuntu:~# chkconfig squid on
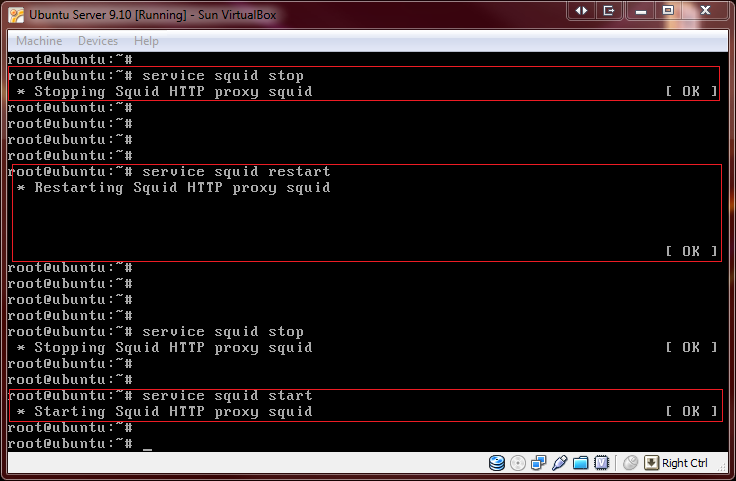
The service command squid start/stop/restart can be used after booting
root@ubuntu:~# service squid start
root@ubuntu:~# service squid stop
root@ubuntu:~# service squid restart
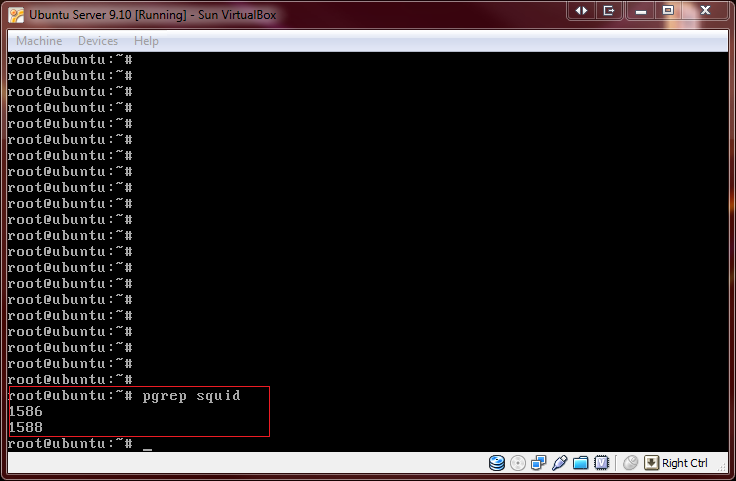
You can test to verify if the Squid process is running with the pgrep command. (To get more info about pgrep, use the man command)
root@ubuntu:~# pgrep squid
If it is working you should be getting a response in plain old process ID numbers (see screen shot).
The main configuration file
The main configuration file for squid is squid.conf. This is where you would want to make changes so squid will behave the way you want. To access this file, enter the following command:
root@ubuntu:~# nano /etc/squid/squid.conf
- note that I am viewing the .conf file with nano.
Restricting Web access
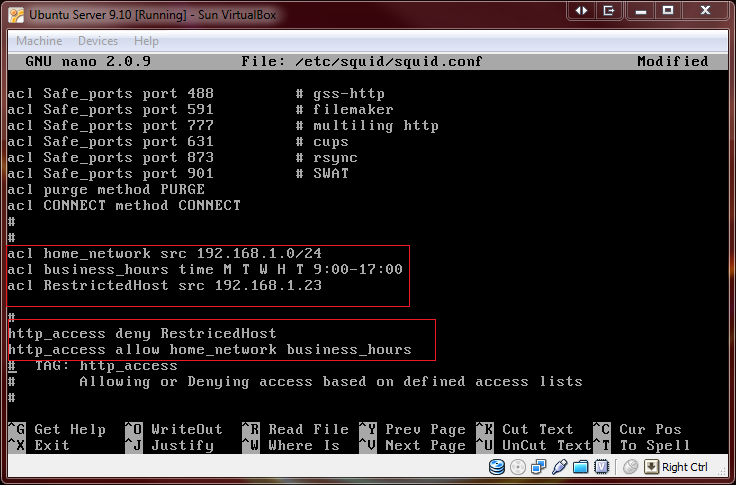
You can create access control lists with time parameters. For example, you can allow only business hour access from the home network, while always restricting access to host 192.168.1.23. Enter the lines that begin with ACL at the bottom of the ACL section to restrict hour access. To restricT access to host 192.168.1.23, enter the lines that begin with HTTP at the top of the HTTP section (See screen shot).
acl home_network src 192.168.1.0/24
acl business_hours time M T W H F 9:00-17:00
acl RestrictedHost src 192.168.1.23
http_access deny RestrictedHost
http_access allow home_network business_hours
Restricting access to specific web sites or domain
We are going create 2 lists in files named /usr/local/etc/allowed-sites.squid and /usr/local/etc/restricted-sites.squid. These two list will be included at the end of the ACL section of the squid.conf file to restrict or allow the websites listed in the files.
These will be the steps:
Step 1 Create the 2 file lists that will include what site or domain we want to restrict (can be created by using touch).
/usr/local/etc/allowed-sites.squid
/usr/local/etc/restricted-sites.squid
Step 2 Include which sites you want to allow or restrict. Of course you will have to insert them in the right file (allowed-sites.squid or restricted-sites.squid)
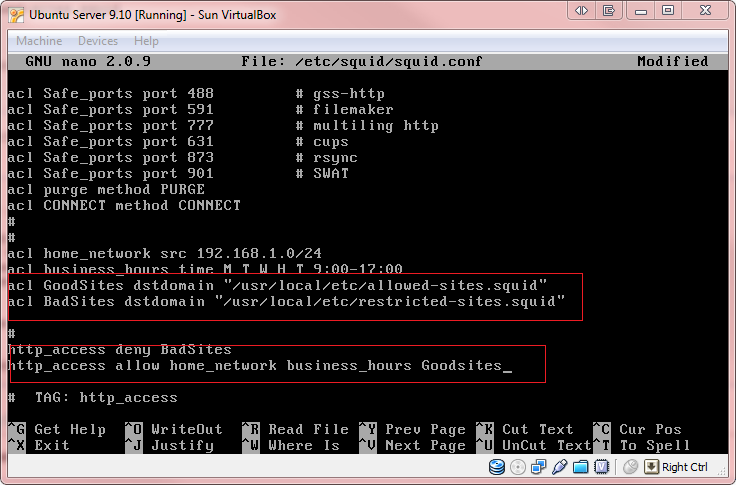
Step 3 We finally get to the part where you will use the files created to restrict or allow access. For that, include these highlighted lines at the end of the ACL part. (We kept the same parameters as before, just added the lines to restrict the sites/domain).
acl home_network src 192.168.1.0/24
acl business_hours time M T W H F 9:00-17:00
acl GoodSites dstdomain "/usr/local/etc/allowed-sites.squid"
acl BadSites dstdomain "/usr/local/etc/restricted-sites.squid"
http_access deny BadSites
http_access allow home_network business_hours GoodSites
Restrict Web Access by IP Address
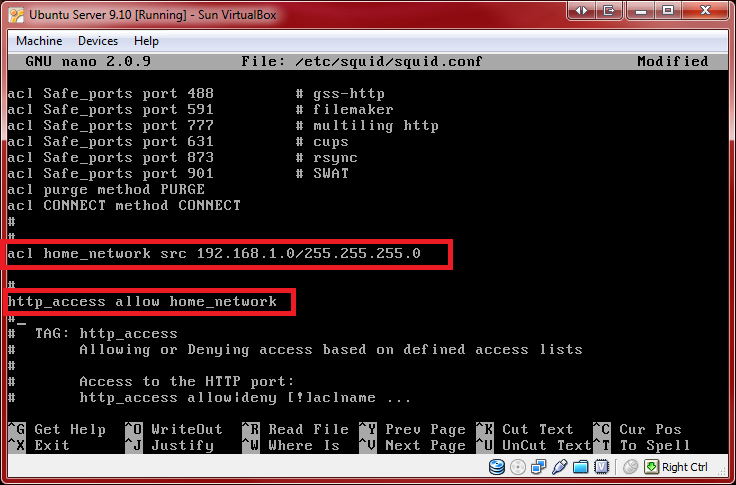
We can also create an access control list that restricts web access to user on certain networks. In this case, it's an ACL that defines a home network of 192.168.1.0
We just have to insert these lines below:
acl home_network src 192.168.1.0/255.255.255.0
http_access allow home_network